Hybrid & Multi-Cloud Strategies: Cloud-Adjacent Secure Gateway
Organizations are shifting to public cloud platforms as part of their digital transformation, expecting to gain significant advantages such as scalability, agility, and possible cost efficiency. This move is designed to align IT infrastructure more closely with business objectives, enabling companies to tailor their technological approaches to meet specific needs while optimizing performance and operational efficiency.

The Challenges
Public clouds offer agility but face challenges in standardizing security due to architectural and operational differences across platforms like AWS, Azure, and GCP. These discrepancies obstruct the cohesion of a multi-cloud strategy and impact the deployment and functioning of security protocols in the following ways:
- Inconsistent policies complicate security across clouds.
- Differing architectures hinder standardization.
- Varied traffic patterns increase management complexity.
- Isolating traffic in shared environments is challenging.
- Pay-per-use costs can escalate with multiple clouds.
- Bandwidth limits affect performance and scalability.
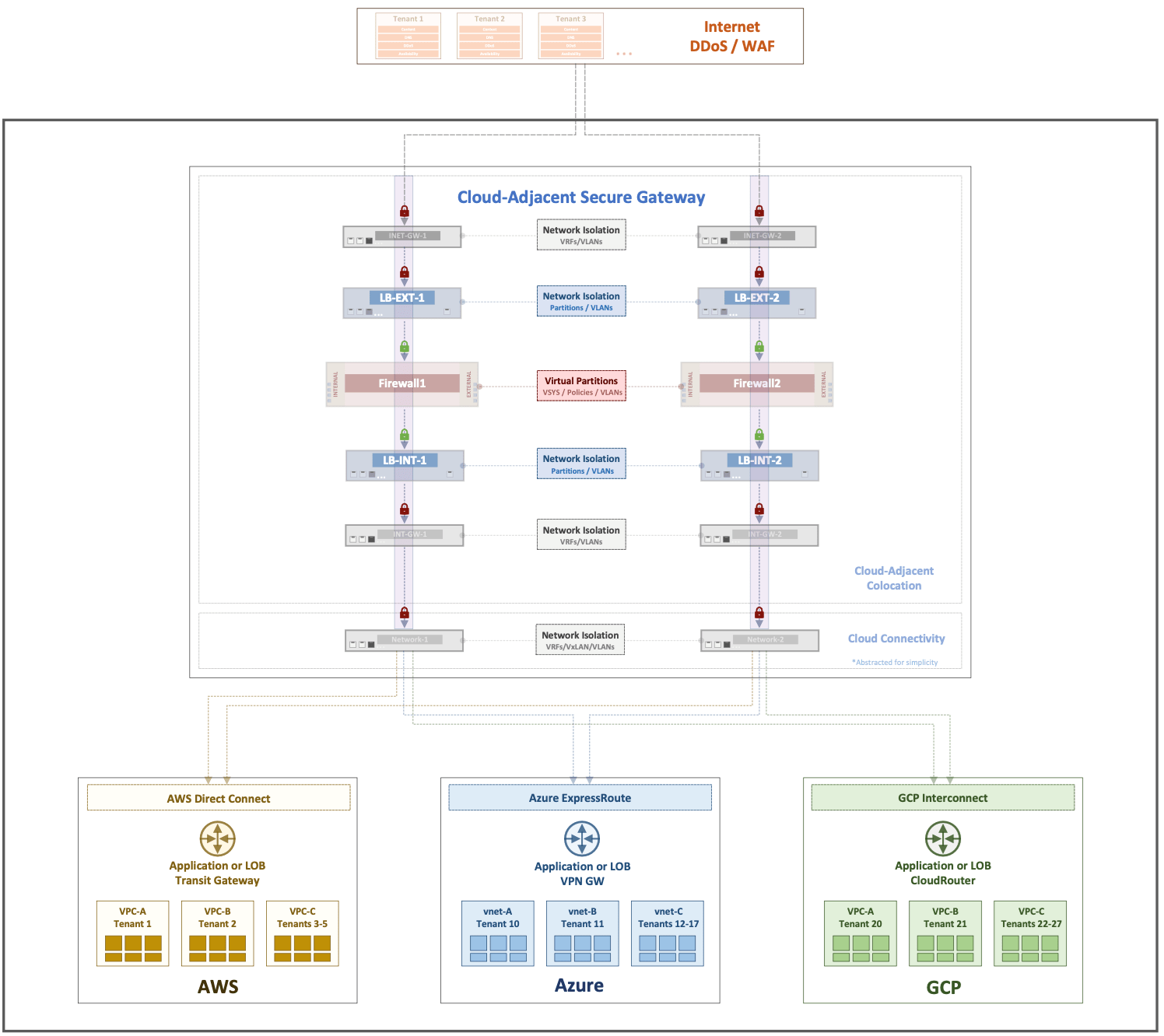
Cloud-Adjacent Secure Gateway Concept
The cloud-adjacent secure gateway strategy shifts key functions like security inspection, encryption, and load balancing from the public cloud to client-owned infrastructure near major cloud providers. This approach offers better control over security and network performance, addresses challenges like inconsistent policies and complex multi-tenancy, and retains the cloud’s agility and scalability benefits.
This strategy introduces a centralized, physically owned gateway for better control and transparency, shifting from dispersed virtual devices. It enhances network management with explicit traffic control and security inspection, ensuring robust security and efficient performance. The architecture includes:
- Gateway Networking: Advanced routing and switching for traffic isolation, multi-tenancy support, and reliable throughput.
- Application Traffic Manipulation: Data steering, load balancing, and managing encryption to optimize security and application performance.
- Security Inspection: Implements security policies, detects malware, filters content, and prevents intrusion for comprehensive threat protection.
- Cloud On-Ramp Connections: Direct connections to public clouds, ensuring high performance and low latency.
Benefits
Building a cloud-adjacent secure gateway brings technological, operational, and financial improvements, paving the way for an in-depth review of these benefits.
- Performance: Provides low latency and high bandwidth cloud access.
- Security: Streamlines policy enforcement and aids compliance.
- Cost Savings: Potential bandwidth and cloud expenses reduction.
- Flexibility and Scalability: Eases scaling and managing cloud security.
- Simplified Management: Reduces operational complexity in multi and hybrid cloud environments.
- Data Control: Provides detailed management of data pathways and sovereignty.

Ryan Lynn
Field CTO, National Accounts
Ryan Lynn is a results-oriented tech professional with expertise in delivering technical solutions that drive value. Recognized as an industry technology leader, he excels in operations, engineering, architecture, strategy, and leadership, leveraging his innovative thinking and problem-solving skills. Ryan’s effective communication fosters strong relationships with stakeholders, advancing business strategies and addressing complex challenges within organizations.
In January 2024, Ryan joined ANM as a Field CTO, a role focused on strategic client engagement and partnering on transformational initiatives. Bringing 25 years of rich experience to ANM, his most recent 12 years were spent as a Field CTO and in various technical leadership roles with another technology partner. Prior to that, he dedicated 13 years to major telecommunications and services providers, where he focused on building large global IT data centers, showcasing his depth of expertise and leadership in the technology sector.
Ryan holds a Master’s degree in Systems Engineering from Regis University, complementing his Bachelor’s degree in Computer Information Systems from Minnesota State University, Mankato, where he also minored in Management.
Key Skills
- Strategic technology consulting
- Strategy and roadmap development
- Technology and business transformation
- Technology change management
- Enterprise architecture and design
Keeping Your Data Safe While Working from Home: Essential Tips
Working from home has become the new norm for many professionals. But while remote work offers flexibility and convenience, it also introduces unique cybersecurity challenges. Protecting your data is crucial to maintaining productivity and safeguarding sensitive...
Considerations when Implementing Disaster Recovery
Implementing a Disaster Recovery (DR) solution is critical for ensuring business continuity in the event of an unforeseen disaster. Whether it's a natural calamity, cyberattack, or system failure, having a robust DR plan can mean the difference between a minor setback...
Understanding the Fundamentals of SASE
Today’s enterprises are rapidly embracing cloud technology and remote workforces, and traditional network architectures are struggling to keep up. As a result, Secure Access Service Edge (SASE) has emerged as a transformative framework that merges network security...