Recap from Ignite’s General Session regarding Copilot and Copilot Studio
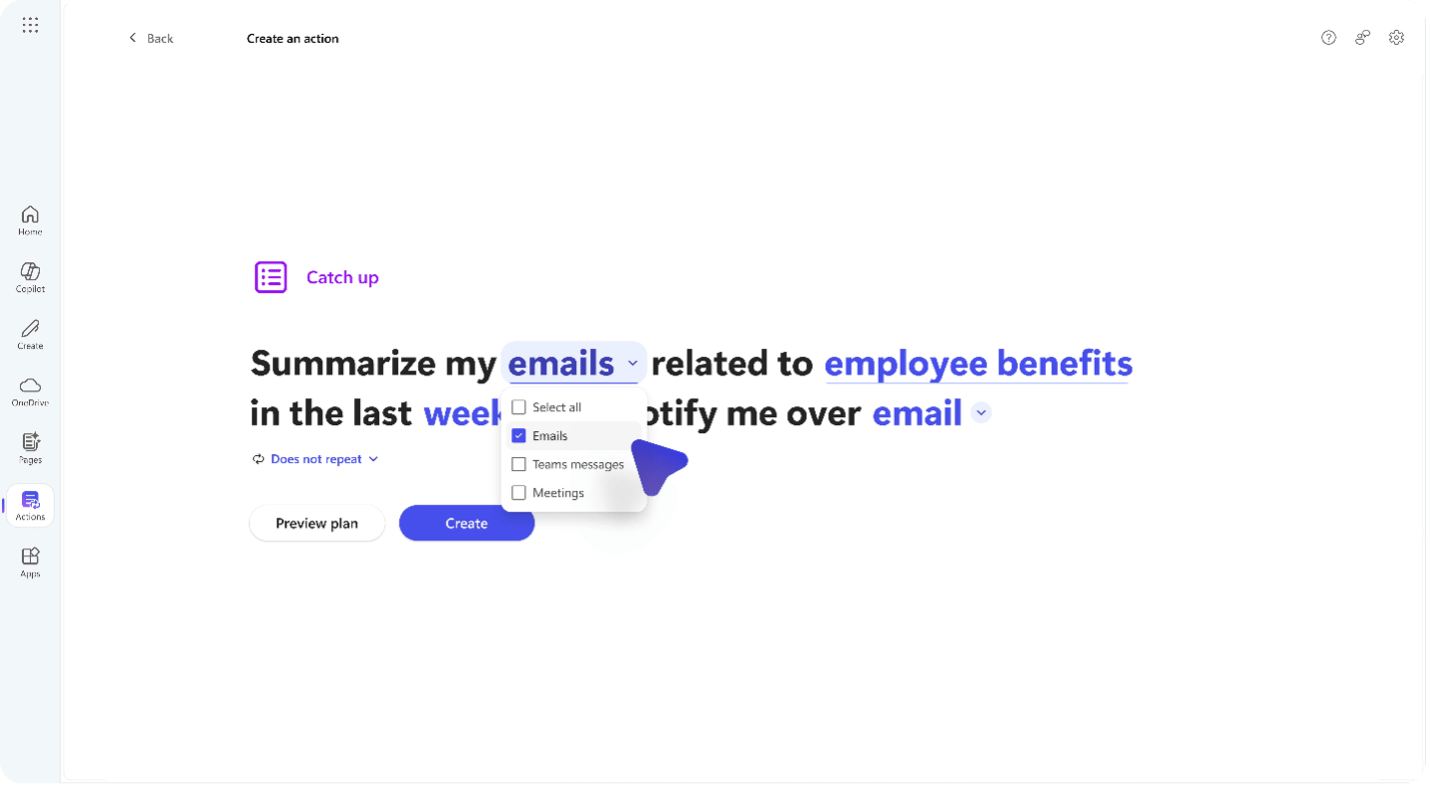
Copilot Actions, https://aka.ms/copilotactions, are similar to Outlook rules but for AI, functioning as “scheduled tasks” for Copilot. It allows automation of everyday tasks with simple prompts that can be set up in advance. For example, a manager with a distributed team working in several time zones can create an action to summarize all the emails received after working hours. These emails can then be prioritized based on relevance, such as customer-related issues or high-priority listings, ready for when the manager signs in the following day.
The capability to create custom Copilot Agents in SharePoint was announced a few months ago and is now generally available (GA). Microsoft also announced some upcoming out-of-the-box agents. The Interpreter Agent in Teams will provide real-time speech-to-speech interpretation during meetings and can simulate the user’s speaking voice. This feature is set to enter Public Preview in early 2025. The Employee Self-Service Agent, which can assist with common policy questions to support HR and IT, is currently in private preview and can be customized with Copilot Studio. The Facilitator Agent, which can take real-time editable notes in Teams meetings and chats, is in public preview. The Project Manager Agent, capable of automating plan creation and task completion in Microsoft Planner, is also in public preview. More out-of-the-box agents are expected to be released in the coming months.

Chris Hinch
Microsoft Practice Director
Prepare Your Organization for AI Readiness
Artificial Intelligence (AI) is increasingly recognized as a critical component for business success. Despite this, many leaders are hesitant to fully embrace AI due to the pressure to demonstrate immediate return on investment (ROI). According to recent surveys, 79%...
ANM Among Less than 1% of Cisco Partners to Achieve Advanced Customer Experience Specialization
ANM announced in March that we achieved the Cisco Advanced Customer Experience Specialized Certification, a significant accomplishment that places ANM among fewer than 1% of Cisco partners in the United States who have earned this certification, underscoring our...
Improve Campus and Student Safety with Security Technology
Using Video Security on School Campuses Prioritizing student safety, teacher safety, and facility safety is a must for schools looking to instill a safe learning environment. Given the prevalence of school-based violence today, school officials shouldn’t wait for an...


