Full-Stack Observability – The Marathon of the Tech World
Full-stack observability? It’s pretty much the marathon of the tech world.
You may have encountered terms such as advanced monitoring, observability, or full-stack observability. But what exactly do they entail, and how do they differ from conventional monitoring approaches?

To define, observability refers to the ability to infer a system’s internal states based on its external outputs.
Full-stack observability offers a comprehensive view across all layers of the tech stack, enabling deep insights into system behavior based on external outputs. In contrast, traditional monitoring focuses on predefined metrics and logs, providing a more surface-level understanding of system health.
To truly grasp the nuances of this space, let’s delve into the architecture of full-stack observability. We’ll explore why it’s essential, who stands to gain from its implementation, the structure it takes, its advantages, the obstacles in its path, and some initial steps toward adoption.
Why Full-Stack Observability?
The landscape of modern IT applications and business services is marked by its complexity, encompassing a multitude of applications, services, and environments. This intricate network, while enabling advanced functionalities and enhanced service delivery, also presents significant challenges in terms of management and oversight. Traditional monitoring approaches, which focus on known parameters and predefined metrics, are increasingly inadequate in this dynamic setting. There’s a growing need to evolve towards a model that emphasizes understanding the unknown—anticipating issues and uncovering hidden problems before they escalate, rather than merely reacting to them.
This shift from a reactive to a proactive stance is crucial across several dimensions of IT operations. Firstly, it’s vital for ensuring an optimal end-user experience; understanding the entire business service chain allows for preemptive identification and resolution of potential disruptions. Similarly, a comprehensive grasp of the security and risk profile across the entire IT ecosystem is imperative. Full-stack observability facilitates this by offering deep insights into every layer and aspect of the IT environment, enabling businesses to not only anticipate and mitigate risks but also optimize operations in alignment with strategic objectives.
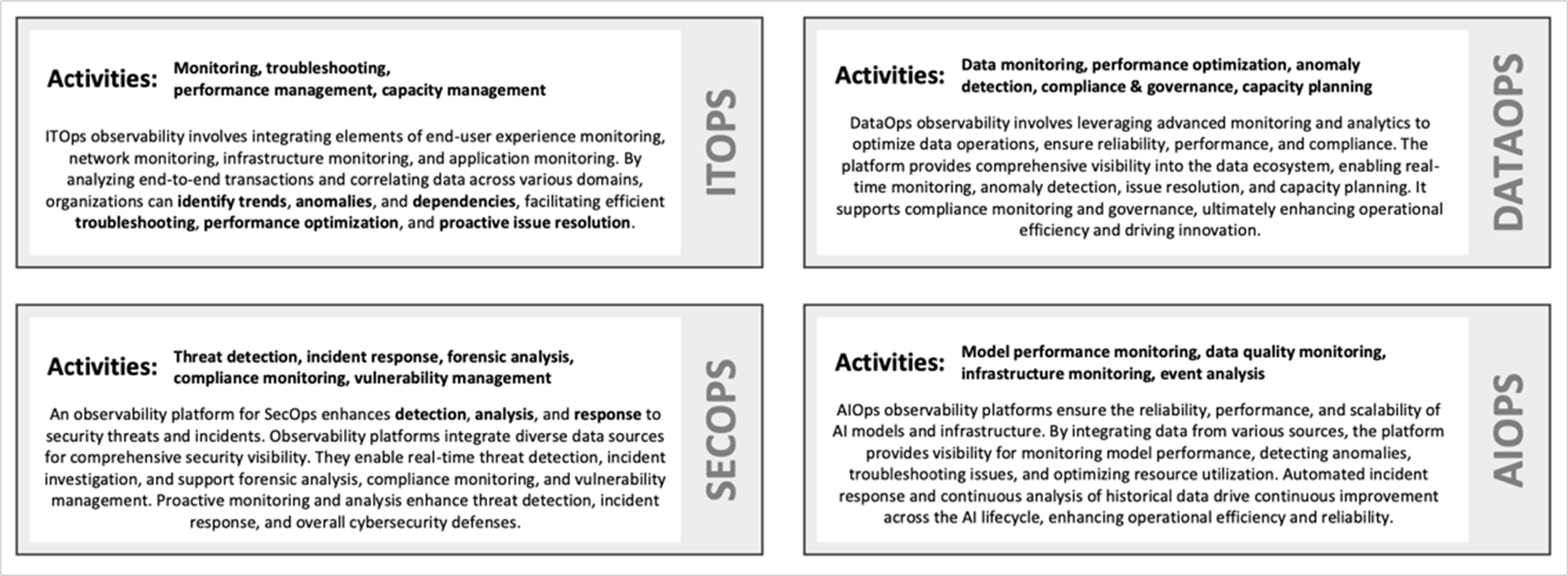
Observability Use Cases
In the realm of full-stack observability, four key use cases stand out, each serving a critical role in the overarching goal of maintaining and enhancing IT and business operations. These use cases are foundational to understanding how observability can be leveraged across different facets of IT management to drive efficiency, security, and innovation.
ITOps: Charged with the smooth operation of business processes through the management of applications, platforms, and infrastructure, IT Operations (ITOps) is the backbone of any organization’s IT ecosystem. Full-stack observability enables ITOps teams to gain a holistic view of the technology stack, ensuring that every component functions optimally and seamlessly integrates with others to support business processes.
SecOps: Security Operations (SecOps) teams are the guardians of the IT landscape, vigilantly monitoring telemetry data from across the IT environment to identify anomalies and security risks before they escalate into breaches. By leveraging observability, SecOps can detect subtle signs of security threats across diverse systems and layers, enabling rapid response and mitigation to protect organizational assets.
DataOps: Observability extends into the realm of Data Operations (DataOps) by providing visibility across the entire data lifecycle—from creation and utilization to deletion. This encompasses ensuring compliance with data governance standards and regulations, a task that requires a comprehensive understanding of data flows, storage, and access within an organization. Through observability, DataOps teams can ensure that data management practices uphold integrity, privacy, and compliance requirements.
AIOps: Artificial Intelligence for IT Operations (AIOps) uses observability data to evaluate the performance and effectiveness of AI/ML data models, training processes, and outcomes. By analyzing operational data through the lens of AI, AIOps teams can pinpoint inefficiencies, optimize model performance, and ensure that AI-driven processes align with business goals and deliver tangible value.
Many companies often begin their journey into full-stack observability with ITOps, given its long-standing role in traditional monitoring scenarios. However, the entry point into full-stack observability can realistically be any of the functional areas, depending on the organization’s specific needs and goals.
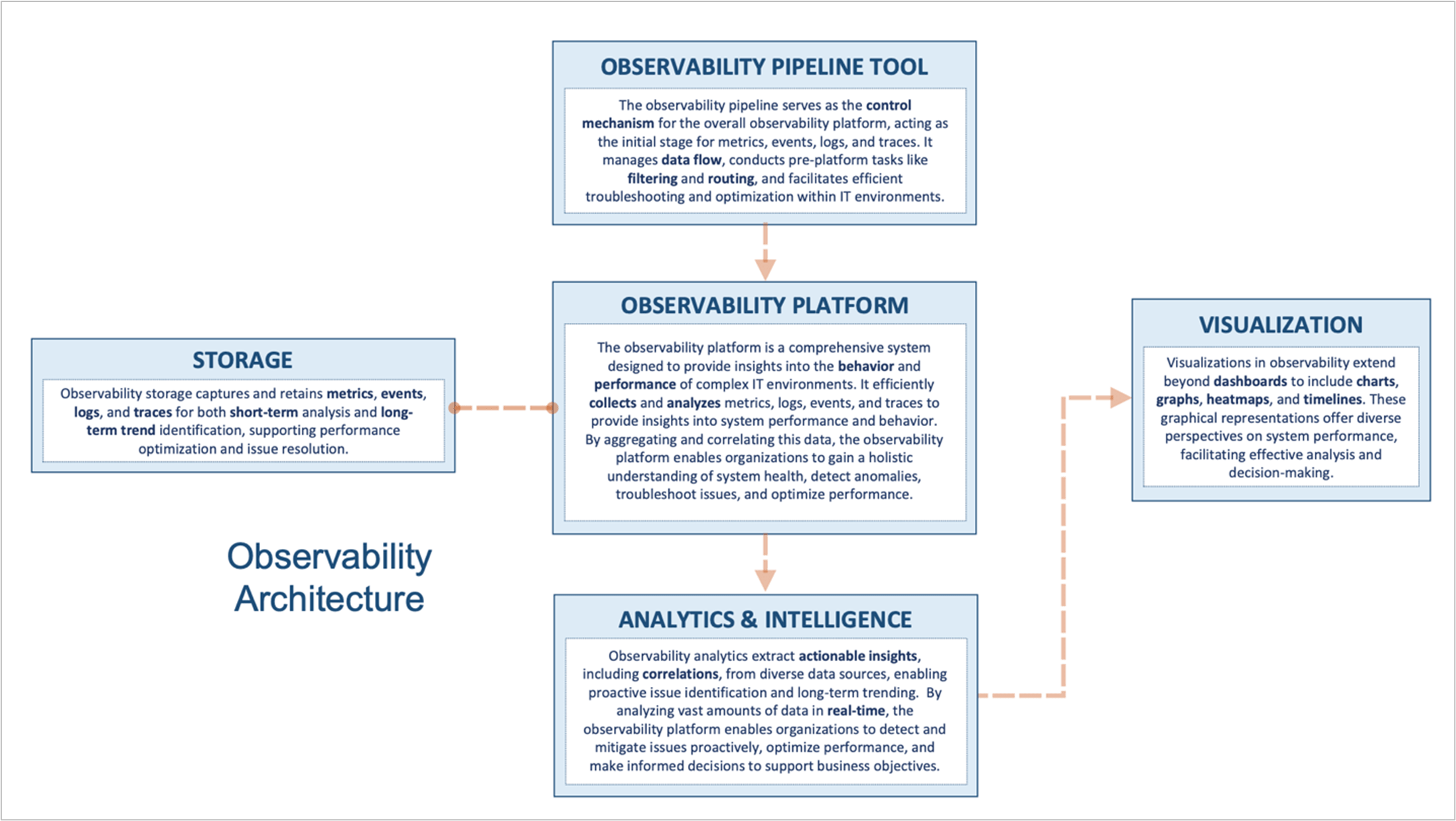
Full-Stack Observability Platform Architecture
The architecture underpinning full-stack observability is both comprehensive and intricate, designed to handle the immense variety and volume of data generated by modern IT environments. At its core, this architecture can be broken down into several key components, each serving a pivotal role in transforming raw data into actionable insights.
Source Data: The foundation of observability lies in the source data, which includes metrics, events, logs, and traces. These data types provide a raw snapshot of system behavior and performance, acting as the initial input for observability analysis.
Observability Pipeline: Once collected, the source data enters the observability pipeline. This critical component is responsible for the normalization, optimization, filtering, and routing of incoming data. It ensures that data is standardized and relevant before it reaches the core platform, enabling efficient analysis and storage.
Observability Platform: At the heart of full-stack observability is the platform itself, which manages the ingestion, processing, and storage of data. Additionally, it provides functionalities for search and matching, allowing users to query and locate specific insights within the vast data repository.
Analytics and Intelligence: This component adds a layer of intelligence to the observability platform, correlating disparate data points and providing business context. It utilizes advanced algorithms and machine learning to identify patterns, predict potential issues, and suggest optimizations, turning data into actionable intelligence.
Visualization Layer: Finally, the visualization layer presents the analyzed data in an accessible and intuitive format. Through dashboards, graphs, and alerts, it allows IT professionals and business leaders to quickly understand the system’s health, performance trends, and areas of concern, facilitating informed decision-making.
It’s worth mentioning that the overall architecture of full-stack observability can differ significantly from one system to another. Certain functions might be merged or might not be present at all, while others could operate more independently and distinctly. Essentially, there’s no “one size fits all” approach to this.
Achieving full-stack observability offers a spectrum of benefits, instrumental in refining and iterating organizational processes and technologies. However, the journey to fully realize these advantages is often marked by a series of challenges that vary from one company to another, depending on their specific operational contexts and maturity levels.
Benefits of Full-Stack Observability:
- Enhanced Application and User Experience: Through improved visibility, performance monitoring, and efficient issue resolution, organizations can significantly boost both application functionality and user satisfaction.
- Improved Security Visibility and Incident Response: Full-stack observability enhances the ability to detect security threats and respond to incidents swiftly, strengthening the overall security posture.
- Enhanced Software Development: By providing increased visibility into development processes, observability helps in identifying errors, performance bottlenecks, and security vulnerabilities, thereby streamlining development workflows.
- Data-Driven Business Decisions: The analysis of telemetry data enables more informed strategic decisions, aligning IT operations with business objectives.
- Collaboration Across Silos: Observability facilitates a collaborative environment by breaking down silos within the organization, promoting a unified effort towards achieving end-to-end visibility.
Challenges in Achieving Full-Stack Observability:
- Organizational Silos: The compartmentalization of teams and resources can hinder the seamless flow of information necessary for effective observability.
- Complexity, Volume, and Velocity of Data: Managing the sheer amount and variety of operational data presents significant challenges in terms of collection, analysis, and storage.
- Diverse Tooling Landscape: The integration of multiple tools, each with different capabilities and compatibility, complicates the observability infrastructure.
- Existing Tech Debt: Legacy systems and technologies may lack the visibility required for comprehensive observability, contributing to gaps in monitoring.
- Cost Implications: The expenses associated with instrumenting systems for observability, processing and storing data, and conducting in-depth analyses can be substantial.
While the path to achieving full-stack observability is fraught with hurdles, the potential rewards in terms of operational efficiency, security, and strategic agility make it a worthwhile endeavor. Organizations must navigate these challenges thoughtfully, leveraging a blend of technology, processes, and culture to harness the full power of observability.
Getting Started
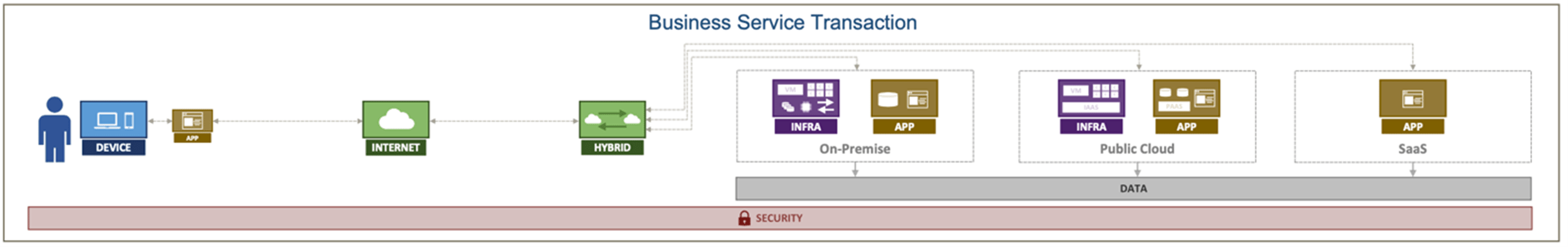
Getting your full-stack observability program going starts with a crucial first steps that’s non-negotiable: business transaction decomposition. This initial process involves identifying and breaking down key business transactions into their functional components, allowing organizations to pinpoint critical areas and determine the necessary telemetry data for monitoring system health and performance.
It’s not enough to perform this step at a single point in time – because the nature of the business and corresponding elements change. It’s vital to develop a strong methodology of continuous analysis and adjustment.
Here are some other steps that are valuable as you look to get your full-stack observability framework going.
- Data Source Strategy: Establishing a telemetry data plan, including what data to collect and how frequently, to ensure relevant and timely insights for full-stack observability.
- Optimizing Processing and Storing Data: Fine-tuning data processing and storage mechanisms to efficiently handle the volume and complexity of operational data in full-stack observability environments.
- Integrating Existing Tools: Incorporating a variety of monitoring and observability tools to create a unified and comprehensive view of the IT landscape.
- Visualizing for Each Use Case: Developing customized visualization methods tailored to each specific use case, facilitating clear and actionable insights for stakeholders.
Final Thoughts
Full-stack observability is hard. 100%.
Achieving its benefits can seem daunting just as training and competing in a marathon is. It demands dedication, discipline, and perseverance, as well as a willingness to push boundaries and overcome obstacles along the way. Just as a marathon runner must continuously refine their technique, endurance, and strategy, organizations must iterate and evolve their observability practices to adapt to changing IT landscapes and business needs.
To finish this race, organizations must do the hard work of understanding their business and the technology that facilitates it. Invest time in decomposing business transactions, identifying critical inspection points, applying business intelligence, and elevating your operational resources to work cross-organizationally to continuously improve the observability workflow.

Ryan Lynn
Field CTO, National Accounts
Ryan Lynn is a results-oriented tech professional with expertise in delivering technical solutions that drive value. Recognized as an industry technology leader, he excels in operations, engineering, architecture, strategy, and leadership, leveraging his innovative thinking and problem-solving skills. Ryan’s effective communication fosters strong relationships with stakeholders, advancing business strategies and addressing complex challenges within organizations.
In January 2024, Ryan joined ANM as a Field CTO, a role focused on strategic client engagement and partnering on transformational initiatives. Bringing 25 years of rich experience to ANM, his most recent 12 years were spent as a Field CTO and in various technical leadership roles with another technology partner. Prior to that, he dedicated 13 years to major telecommunications and services providers, where he focused on building large global IT data centers, showcasing his depth of expertise and leadership in the technology sector.
Ryan holds a Master’s degree in Systems Engineering from Regis University, complementing his Bachelor’s degree in Computer Information Systems from Minnesota State University, Mankato, where he also minored in Management.
Key Skills
- Strategic technology consulting
- Strategy and roadmap development
- Technology and business transformation
- Technology change management
- Enterprise architecture and design
Protecting Your Organization from BYOAI: Key Takeaways from Our Recent Webinar
The rise of generative AI has brought both opportunities and challenges. During our recent webinar, "Protect Against BYOAI & Shadow IT with Microsoft Defender," we dove into the critical aspects of safeguarding your organization from the risks associated with...
The Growing Cybersecurity Threat in Healthcare
The healthcare sector is increasingly becoming a prime target for cyber-attacks, with dire consequences that extend beyond financial damage. The FBI and Department of Justice now classify cyber-attacks on healthcare as “threat to life” crimes due to their potential to...
MSSP vs. MDR: Which is Right for Your Business?
As cybersecurity becomes more complex, organizations are increasingly turning to third-party providers to help manage their security needs. Two popular options for outsourced cybersecurity are Managed Security Service Providers (MSSPs) and Managed Detection and...